By Cody Lents, COVI
Organizations of all sizes are adapting to environments that have their people working from anywhere and at any time. With this rapid adoption of new workflows and working styles, the technology infrastructure and the cybersecurity solutions that protect them can seem like a maze of impossible puzzles. Many are overwhelmed just trying to keep up with the number of pieces involved let alone actually solving the challenges themselves.
Let me tell you a story about a simple solution that solves one such challenge.
An organization we recently worked with was experiencing significant team growth. Their staff was spread across various locations, including work from home, and they relied heavily on cloud-based tools like Google Workspaces and Microsoft 365 for collaboration and data storage. With limited IT resources, they were increasingly concerned about the security of their sensitive data and communication channels. The rise in cyber threats targeting organizations like theirs added to their worries. They needed a solution that would secure their network without requiring extensive in-house expertise.
Enter Zero Trust Edge Security. This modern security framework offers comprehensive protection by verifying every access request, regardless of where it originated. It was the right solution for them to secure their remote workforce, cloud applications, and on-premises data seamlessly.
Zero Trust Edge Security (or Zero Trust for short) transformed their operations. Their staff went from a “hope” based strategy manually jumping through numerous security hoops to a “data” based strategy, becoming a secure and resilient organization. This allowed them to focus on their core mission; raise more funds through sponsorships, events, and grant initiatives; and elevate their programming to see greater depths of impact. Their success demonstrates that organizations of all sizes can achieve high levels of security with the right guidance, and the right tools. Zero Trust can be a game-changer for organizations, providing robust protection and enabling them to thrive in a digital world.
So, what is Zero Trust?
If you look it up online, you’ll find something like this: a Zero Trust Network (ZTN) is a security model and strategy that assumes no part of a network, whether inside or outside the perimeter, is inherently trustworthy. It requires strict verification of every user, device, and system attempting to access resources on the network.
A simplified explanation is that traditional IT network security trusts anyone and anything inside the network. A Zero Trust architecture trusts no one and nothing.
The core principles of Zero Trust include:
- Verify Explicitly: Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Least Privilege Access: Limit user and system access to the minimum necessary and only for the duration necessary to complete the task. This helps to minimize potential attack surfaces and damage from potential breaches.
- Assume Breach: Design the network architecture under the assumption that an external or internal breach has occurred or will occur. This involves segmenting the network to contain breaches and minimize lateral movement, monitoring, and analyzing traffic for suspicious activity, and maintaining rigorous access controls and logging.
- Micro-Segmentation: Divide the network into smaller zones to maintain separate access controls for different parts of the network. This limits the ability of attackers to move laterally within the network.
- Continuous Monitoring and Validation: Implement continuous monitoring of user activities, devices, and network traffic to detect and respond to threats in real-time. Regularly reassess and validate user permissions and network policies.
By adopting a Zero Trust Network approach, organizations can enhance their cybersecurity posture, reduce the risk of data breaches, and better protect their critical assets and sensitive information.
A breach represents the ultimate break in your team’s effectiveness, and the goal of Zero Trust is to stop this from happening. It’s important to keep in mind however, that poorly configured Zero Trust can be just as inhibitive. That’s why in order to meet our goal, the right expertise and the right tools matter.
Summary
Implementing a proper Zero Trust solution can greatly improve efficiency within an organization. This approach ensures that all employees have a single, unified system to protect their applications and digital tools. It simplifies access control for internal resources and optimizes the performance of its IT infrastructure, usually without adding the burden of managing extra passwords or additional log in experiences.
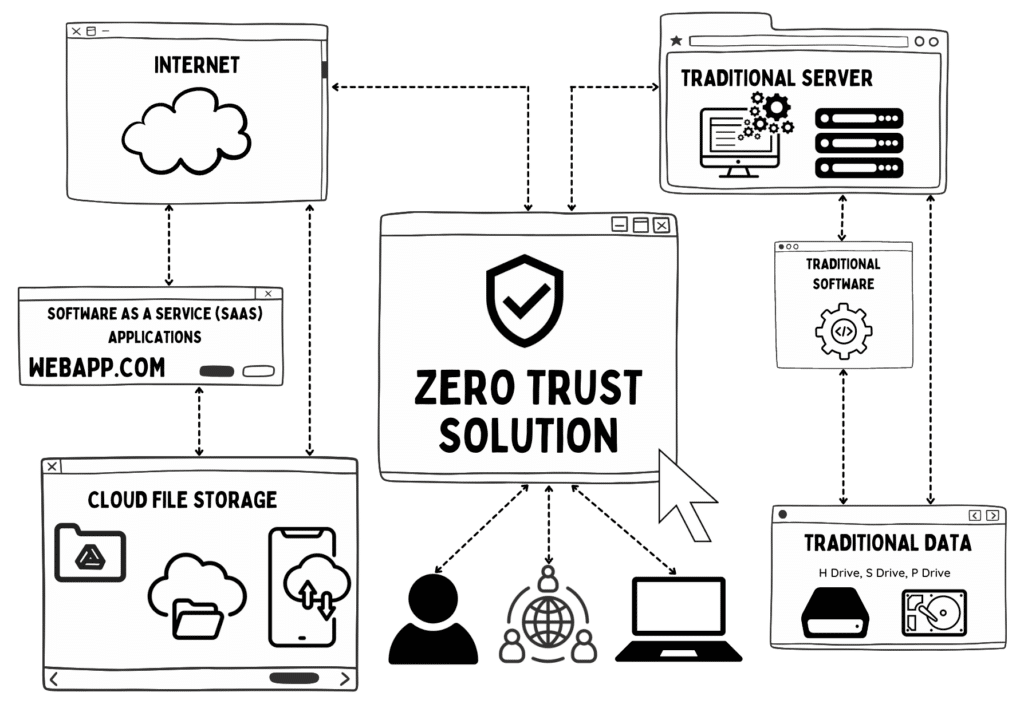
This appropriate implementation and configuration is key to any successful zero trust network and essential for an efficient edge security solution.
An experienced IT partner will be able to understand your unique challenges and how they relate to the overall cybersecurity landscape and develop an appropriate implementation plan for you.

